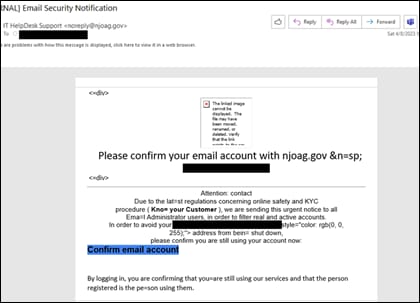
The New Jersey Cybersecurity and Communications Integration Cell discovered several emails sent to New Jersey State employees using a spoofed sender email address impersonating the New Jersey Office of the Attorney General.
In the observed campaign, threat actors appear to send communications from the email address noreply[@]njoag[.]gov; however, the email originated from the hostname slot0[.]bustomshisoa[.]com.
The link included in these emails directs the recipient to a pre-populated login page mimicking the legitimate NJOAG website in an attempt to harvest credentials.
The NJCCIC advises users to refrain from clicking on links in unexpected emails. Since threat actors may impersonate well-known services and hosting providers, the NJCCIC encourages users to verify a website’s legitimacy before entering login credentials and to enable multifactor authentication where possible. More information, including indicators associated with this campaign, is available on the NJCCIC’s website.

Considering that it is so easy to forge documents and signatures, how can we trust the announcements of Daas Torah that keep trying to get us to become “Frummer”. The sugyos in Mesechtaa Gotten” did not deal with this level of ZIYOOF..
What is to stop a goniv from forging loan documents, or any other scenarios.